TL;DR
It is worth thinking about how you do the following for access to all your systems for customers, staff, third parties and guests:
Access request.
Access approval.
Access provisioning and deprovisioning.
Access review.
Entitlement/role composition review.
Segregation of duties and toxic combinations (standard and privileged access).
Access monitoring.
Identity lifecycle management (joiner, leaver and movers).
Account management (account unlock, enablement etc.)
Self service password reset (SSPR).
Password and MFA factor registration.
Invest in an Identity Governance and Administration (IGA) solution for staff/third parties/guests and for Customers (usually different instances). So much of even “privileged access” is actually delivered via your IGA system. Protect your front door, everything else you do in cyber security is pointless without this. Every project and system change or implementation will need this. It has a high risk reduction benefit and even usability and cost/complexity reduction so the business case is relatively easy.
Disclaimer: any product or service mentioned is my own opinion. I write this for the joy of writing and as a memory aid. This is a mostly free blog (everyone has to eat), I have no affiliate links, nor receive endorsements for anything I say here. Caveat Emptor. This is also a light hearted blog. I’m trying to be funny, hopefully it works. I have a conversational style, hopefully I use enough commas. But I also love feedback so let me know what can improve.
I’m the co-founder of Identity Revive. We can help you:
Understand your requirements and help you secure the front door for all your systems and delight your customers and workforce with access that just works.
Architect, design, deliver and run your cyber security controls in code so you are compliant with regulation and don't suffer from a cyber incident.
Make sure you are getting value out of your Managed Service Providers (MSP’s) and help them use less ClickOps so you get charged less and they make fewer errors.
Also remember if you are a Not-For-Profit (NFP) or in Education or Health sectors as an Non-Government-Organization (NGO), we provide free consulting as a way to Give Back to the community and our Country (Australia). Email me at: rakkhi@identityrevive.com .
I also write more frequent Substack notes: If you like more shortform i.e. Twitter / X like.
Substack has a chat feature now: If you want to talk with me and ask me questions.
Introduction
Unfortunately many CISO’s and even security architects do not “get” identity.
Even where they do, identity == authentication == Okta, Active Directory, Azure AD etc.
The really hard part of identity is the access management lifecycle or identity governance and administration.
This is also the part, in addition to logging and monitoring, that will apply to your all your non publicly accessible systems, so it is worth your while to learn about it and invest in it.
What is Identity Governance and Administration (IGA)?
It basically consists of people, processes and systems for:
Access request (including birthright and role based access) - you need a way for people and machines to request access at minimum. As organizations mature you want to provide people access as they join the organization (e.g. Internet access, Intranet access, Learning and Education system, HR and Payroll systems) and when they move into roles (e.g. make your $3000/day DBA or Cloud Engineer or Quant AI/ML Engineer productive on Day 1, or you know delight your customers, make guest wifi access “just work”). Your amazing self-service no code / low code ML models produced by your business needs access to go live… You want this to be efficient and secure.
Access approval - Access needs to be approved by a human or pre-approved as birthright or as part of a business role/position in the organization.
Access provisioning and deprovisioning - access needs to be granted or removed in all target systems or a centralized system they use (e.g. Azure AD or Active Directory groups). In many organizations this can be 2000+ different systems. This is the real reason for the iceberg metaphor above. Managing connectors to this many disparate systems, with so many different schemas is really hard. And yeah… SCIM does not cut the mustard in most organizations because … ah.. not everything is web and hardly any system even supports SCIM, it doesn't support nested groups etc. This includes managing access to Operational Technology (OT) / Industrial Control Systems (ICS) in addition to IT which might only have an IP address as “authentication”. So to grant users access to this system you need to add a safelist IP to a firewall group. An IGA system can do this.
Access review - Your leavers and movers process won’t always work especially for Third Party users or Customers where you don’t have a link to their HR/CRM system. So review access periodically and on a trigger e.g. when someone moves roles or offices.
Segregation of duties and toxic combinations - certain combinations of access should not be held together. The classic example is back-office and front-office in a bank. Certain staff should not be able to access all customer information is another example. You want to master these policies or rules in your IGA system and be able to detect and prevent these combinations of access being granted or revoke/certify if they exist.
Access monitoring - it is very hard to grant the minimum required access (least privilege principle holy grail). You want to be able to compare access actually used vs what is granted to enable you to get to least privilege over time. Also one of the first things an attacker does after initial entry is try to get a legitimate account with administrator privileges. You want to monitor for that.
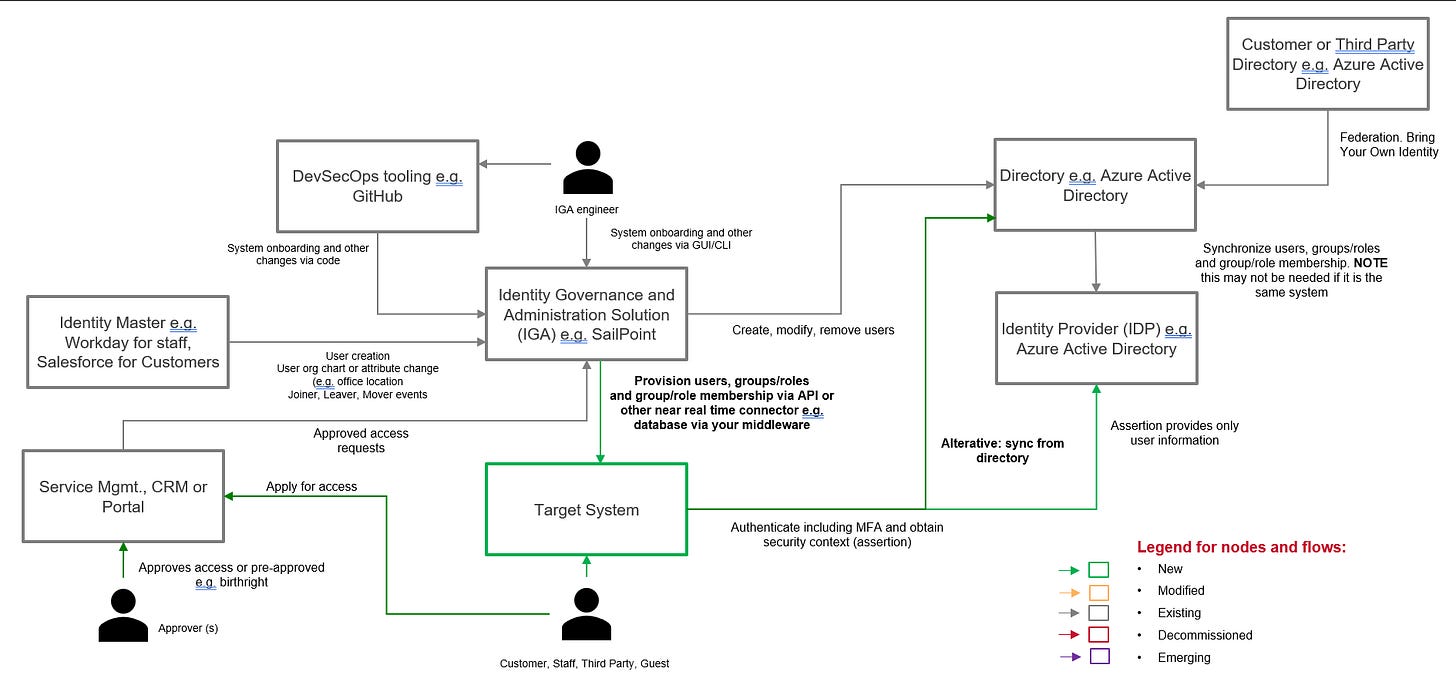
Access or Identity Lifecycle patterns
You want to build something like this:
That way every new system you introduce or change has a standard way of managing their access lifecycle. This applies to all systems (IT, OT, customer, guest etc.) and all classes of users:
Benefits
So what? What does it mean for me? Why invest in IGA?
Regulation - when all else fails as a selling point. Governments around the world are increasing regulation for data breaches. Good for selling to CISO’s, GM’s, Boards that won’t care about anything else. Avoiding a 30% of revenue or $50m fine seems like a good thing. Even spending $250k year cost benefit works out even if you think the probability of a breach at your company or one of your third parties is low ($50m x 1% == $500,000)
Reduce risk, protect your reputation - ultimately what else do we have in this world other than our word? Trust is everything.
Even if you get your money back, your share price goes back up, customers, partners, governments remember. Ultimately whatever you outsource, whatever your cyber breach insurance is, your company is accountable.
User experience - refer above. It is amazing when technology “just works”.
Do the math: $1500/day staff member x 40 hours to get all their access working vs. their access just works on day one. Same with when they move roles. Your customer signs up and all their access “just works”. Not to mention the qualitative “engagement” benefit and avoidance of frustration.
Speed to market - when you have the above architecture setup and working smoothly adding new systems for any of your users: customers, third parties, staff, guests is just so much easier and faster. What do all your IT projects have in common? Need to provide someone access, want to log what they do.
IGA solutions
These companies are good but not perfect:
You could also build your own (more flexibility but requires some good engineers):
Or build it with ServiceNow workflows, or Power Automate or PowerShell scripts.. there are options for every budget and IT skills. In general though if you can make a business case, want all the features and benefits I mention above and want to focus on your core business rather than maintaining software I would highly recommend investing in one of the above tools. You can always get a partner to run it for you.
Conclusion
Prioritize investing in identity governance and access lifecycle management. Not only is it a great way to reduce risk and stay compliant it is also great for reducing friction and delighting your staff, third parties, customers and guests. Identity is your front door of cyber security. Make sure yours is closed and only allowing the right people in. Contact me if you want help.